Yup, Developer Day 2024 is a wrap!
We hosted a 24-hour virtual event with unique content regardless of your timezone! But do not despair— if you want to go back, you can check out the announcements, all sessions and labs. In the meantime, let's take a look at some of the cool stuff Auth0 announced and what is new with the product!
🤑 Improvements in Pricing & Plans
Let's start with (what I think) is one of the best announcements 😏. We heard the feedback from developers, and we want to make application security accessible to everyone, so we're adjusting pricing and what's included in plans in response. So, let's take a look at some of the changes in our plans:
Expanding Free Tier
What's included in the new plan?: - Increase in the number of Monthly Active Users (MAUs) from 7,500 to 25,000 MAUs. - Now you have unlimited social connections and Okta connections. - You can have up to 5 Organizations and use Passwordless. - You can set up to 5 Actions. - You can configure your own custom domain.
Expanding Paid Plans
- Organizations are included in every plan, with sign-up and login customization starting from the B2C Essentials plan. You have unlimited Okta connections, which allow you to integrate your applications easily with Okta Workforce Identity Cloud.
- MFA included in all Enterprise plans!
🚀 Login Experience & Extensibility
Every company has its own authentication requirements, and Auth0 wants to make sure most of them, if not all, are available, so let's take a look at some improvements:
Add Custom Prompts to Sign-Up and Login
You can now add custom prompts to your sign-up and login boxes. Now you could, for example, add extra user information like their full name, phone-number, without leaving the authentication process. You could also show them a prompt with your Terms and Conditions so they can consent before registration. Most importantly, you can validate all the data you gather using Auth0 Actions!
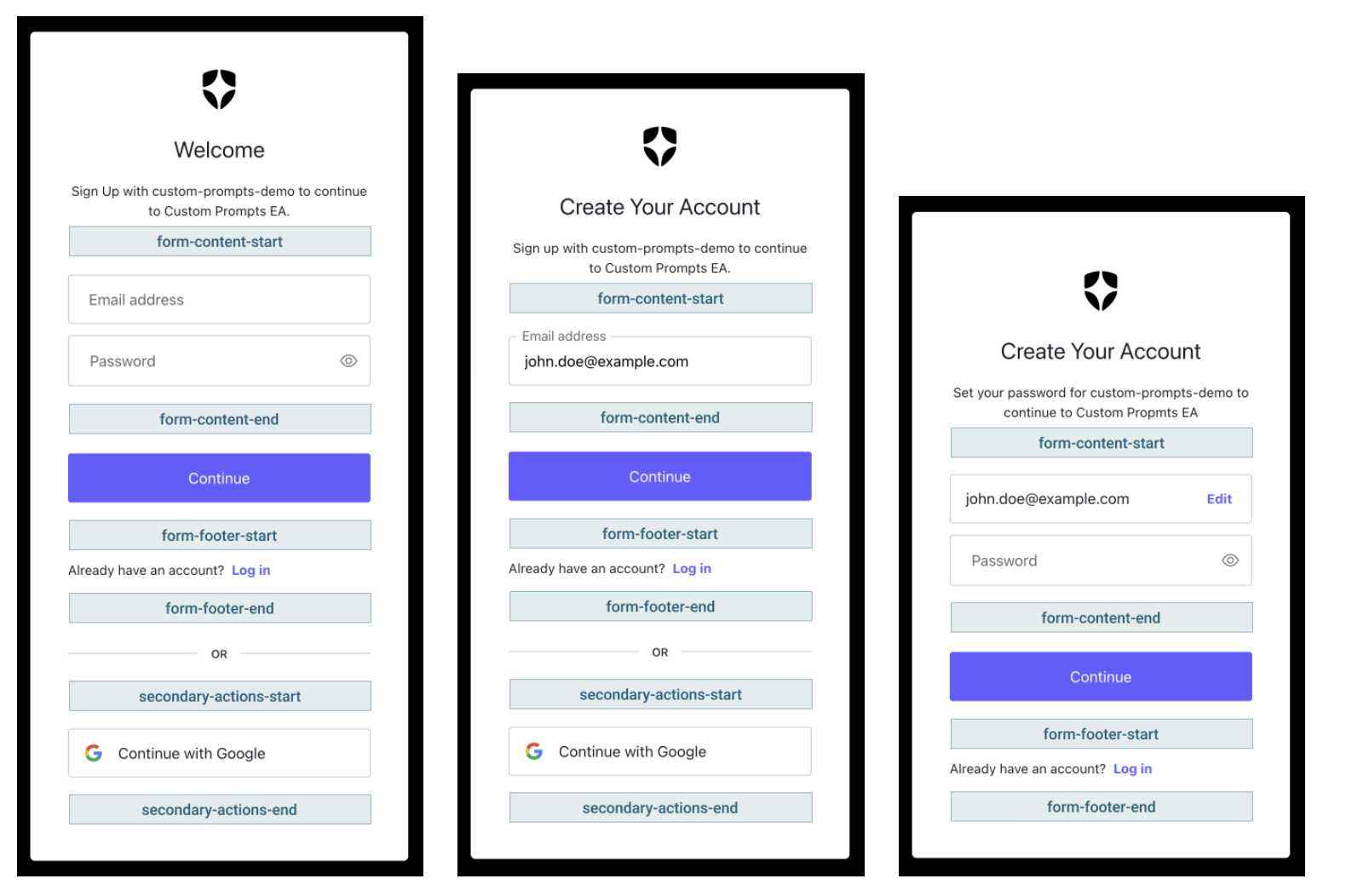
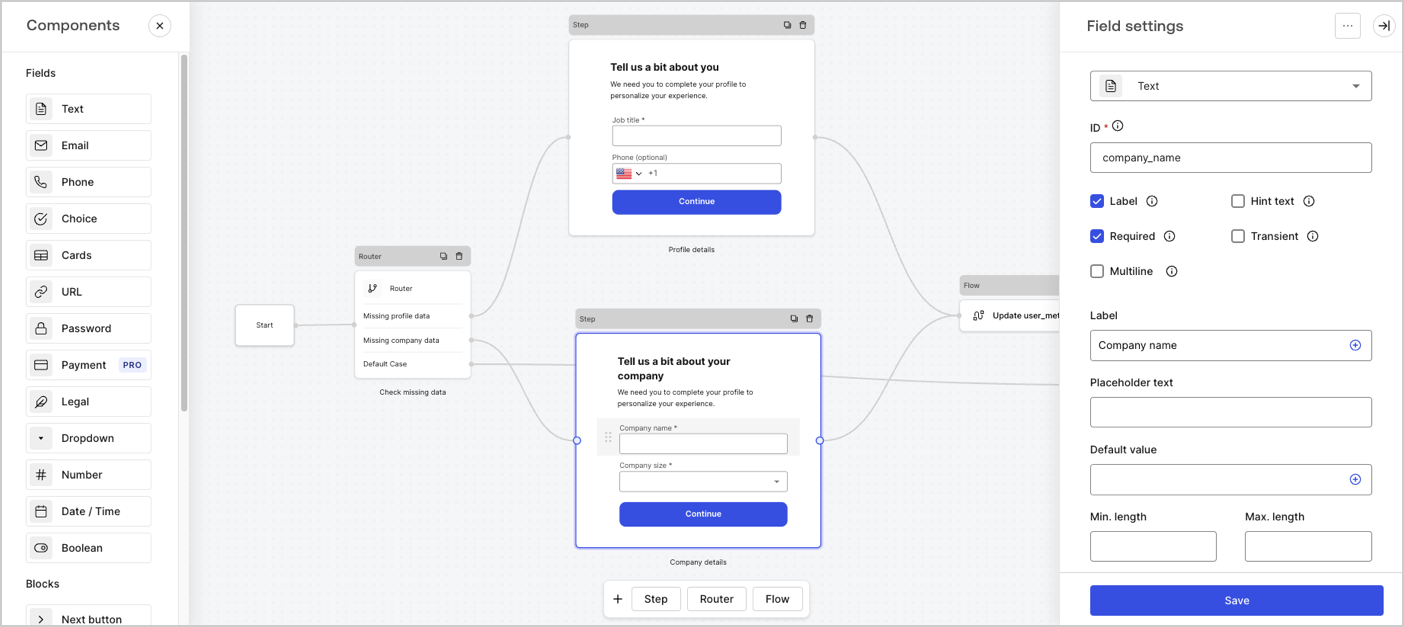
Auth0 Forms
Auth0 Forms allows you to create custom forms and extend your identity flow using a visual editor. You no longer need to redirect your users outside of Auth0 to achieve this. Check out the docs here to learn how to do it.
🚦 MFA Customization with Actions
Now, you can enroll your users in specific factors using the post-login flow in Actions. You can also prompt users to enroll in SMS for one application while encouraging them to enroll in push notifications or WebAuthn for a different application. Learn more on how to customize MFA here.
🤩 New APIs: Sessions & Refresh Tokens Management APIs
We've released new APIs! Here's everything you need to know:
Session Management API
The Sessions Management API provides you a set of endpoints of the Management API that allows you to manage active authenticated sessions, enabling you to close those deemed redundant or a security risk.
Refresh Tokens Management API
The Refresh Tokens Management API allows you to list and revoke refresh tokens and make your applications more secure and consistent.
🔐 New Features in Okta FGA
Earlier this year, we released Okta FGA, a highly scalable authorization service powered by OpenFGA; apart from that, the team has been working hard to add more features:
- Create multiple credentials for a single Okta FGA store with different permissions depending on how you want to use it. You can learn more about how to do this by reading the docs.
- Modular Models so you can compose an authorization model from multiple modules; this feature comes in handy in scenarios where your authorization model grows too large, and it isn't easy to understand or when your team grows, and ownership boundaries are not clear enough.
🏢 Highly Regulated Identity (HRI)
Highly Regulated Identity is Auth0’s feature set that enables the development of secure applications that comply with critical international regulations such as Open Banking, Financial Data Exchange, and Consumer Data Rights. It is now available as an optional security add-on for Enterprise plan customers.
Among other things, Highly Regulated Identity provides you with the following: - Advanced security with OpenID Connect. - Strong Customer Authentication, which supports compliance with Europe’s Payment Services Directive (PSD2) - Strong Application Authentication allows you to implement the FAPI 1 Advanced Security profile using Private Key JWT or mTLS for OAuth. - Token Binding adds the ability to bind an access token to your application, preventing unauthorized access even when a token is compromised.
🤖 Bot Detection Improvements
We are introducing Auth Challenge, a new and improved bot response available in Bot Detection.
Auth Challenge is the default bot detection response, which provides a CAPTCHA-free user verification. It leverages a series of non-intrusive browser challenges to set the difficulty of the challenge, making it tougher on bots and easy for humans. You can learn more about it in the Bot Detection docs.
👥 Introducing Auth0 Teams
Auth0 Teams provides a single point of visibility and control over your Auth0 resources by providing centralized governance, compliance, and secure collaboration at scale.
Teams consolidate managing tenants, tenant members, and subscriptions in one central place, offering visibility from a higher level perspective instead of the tenant by the tenant. Auth0 Teams is designed to improve the work efficiency and experience of dashboard admins responsible for managing the Auth0 resources.
Learn more of Auth0 Teams in our docs!
👩💻 JWT Access Token Profiles
JSON Web Token (JWT) Profile for OAuth 2.0 Access Tokens - RFC 9068 is now available. RFC 9068 provides a standard JWT format to represent Access Tokens. The main goal here is to provide interoperability to issue and consume Access Tokens between authorization servers and resource/API servers of different vendors and reduce friction to use Auth0 when onboarding from other solutions. Read more about it in the docs.
Our Auth0 profile for JWT Access Tokens will remain the default option, as we need and want to maintain backward compatibility. However, customers can now opt-in to use the new profile for Access Tokens on a per-API basis. This standard was authored by Vittorio Bertocci.
Summary
This blog post was already a summary of everything announced during Developer Day 2024, so go back and check the section names! 😜
If you missed Developer Day and watch to catch the recording, you can do so by clicking here.
About the author

Carla Urrea Stabile
Senior Developer Advocate
I've been working as a software engineer since 2014, particularly as a backend engineer and doing system design. I consider myself a language-agnostic developer but if I had to choose, I like to work with Ruby, Python, and Elixir.
After realizing how fun it was to create content and share experiences with the developer community I made the switch to Developer Advocacy. I like to learn and work with new technologies.
When I'm not coding or creating content you could probably find me going on a bike ride, hiking, or just hanging out with my dog, Dasha.
